Microsoft Open-Sources Rust-Written OpenHCL For Running Confidential Intel/AMD VMs
Microsoft announced today the new and now open-source OpenHCL paravisor for the virtualization stack for enabling Intel TDX and AMD SEV-SNP confidential computing virtual machines (VMs) with this Rust-written software stack. This effort by Microsoft has been five years in the making and is now open-source and will continue to be developed in the open.
OpenHCL is an execution environment that serves as a paravisor to confidential computing VMs with hardware protections provided by AMD SEV-SNP or Intel TDX. OpenHCL can run though on both x86_64 and ARM64 although currently just supporting the Intel and AMD confidential computing platforms. The plan on the ARM64 side is for supporting Arm CCA (Confidential Compute Architecture). And, yes, Linux is supported alongside Windows. OpenHCL is already in use on Azure.
Microsoft explains in their release today of this from-scratch software:
Today, OpenHCL can run on both x86-64 and ARM64 platforms, and it has support for Intel TDX and AMD SEV-SNP confidential computing platforms. OpenHCL runs in the L1 VMM of a TDX confidential VM and in the VMPL0 of an SEV-SNP confidential VM. See the OpenHCL user guide for step-by-step instructions to use it. OpenHCL offers a rich set of powerful services to both confidential and non-confidential VMs alike:
- Device emulation via standard device interfaces, essentially offering a set of emulated devices, such as vTPM and serial.
- Device translation via standard device interfaces, such as NVMe to para-virtualized SCSI, allowing assignment of hardware devices directly to VMs (accelerated IO) without requiring guest OS changes - enabling VMs to take advantage of the performance of cutting-edge devices.
- Diagnostics support, particularly useful to allow debugging confidential VMs where it is difficult to use traditional methods of debugging.
(To confidential VMs specifically) Support for guests that are not fully enlightened - such as Windows and older versions of Linux - to run on confidential computing platforms via standard architectural interfaces.
For confidential VMs, even though OpenHCL unlocks amazing value to guests that are not fully enlightened (by enabling them), in the future OpenHCL could also provide a lot of value to fully enlightened guests by providing them with any or all its other services as different scenarios require it.
...
OpenHCL is composed of several open-source components, the most important one being OpenVMM, the cross platform, virtual machine monitor (VMM) project written in Rust. This VMM runs several user mode processes to power OpenHCL. Running a VMM inside OpenHCL allows us to support guests with assigned devices and provide device translation support. Additionally, it allows us to share confidential and non-confidential architecture. We run the same VMM in the same environment for both confidential and non-confidential guests, and the VMM provides the same services tailored to their requirements. This avoids fragmented virtualization solutions among confidential and non-confidential VMs, moving towards closing the feature gaps of confidential VMs.
Or this convenient diagram for explaining the virtualization stack:
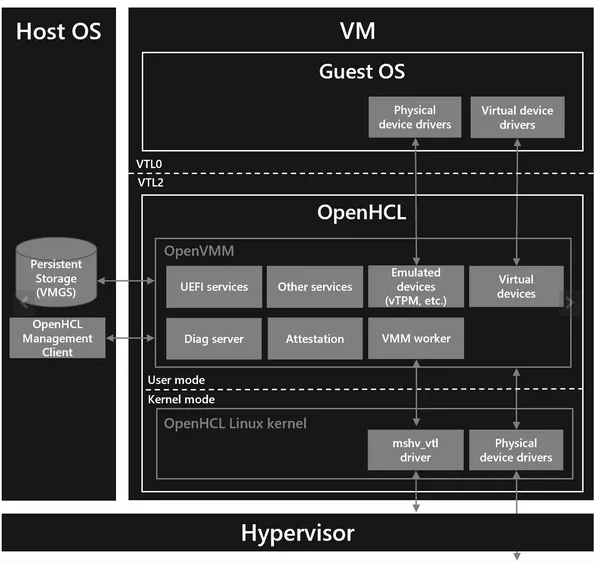
More details on the OpenHCL release and its open-sourcing via the Microsoft Tech Community blog. The OpenHCL code is open-source via the Microsoft OpenVMM project on GitHub.
 Pre Sales:Mr.Qian
Pre Sales:Mr.Qian